Azure AD OIDC Integration
Learn how to configure a connection to Azure AD via OIDC.
Introduction
Each SSO Identity Provider requires specific information to create and configure a new Connection (through Application registered). Often, the information required to create a connection will differ by Identity Provider.
Azure AD integration with Cripsa using OIDC consists of 4 parts,
- 1. Create a project/select (an existing) project by logging into https://cripsa.com
- 2. Create an App in Azure AD using admin account in https://portal.azure.com/
- 3. Use Client Credential (ClientId and ClientSecret) and OIDC Issuer information information of the Azure AD App registered to integrate it with Cripsa.
- 4. Use the Final URI received to call against the User click to start the Authentication process.
Create Project through Cripsa
Login to Cripsa Dashboard by using email account
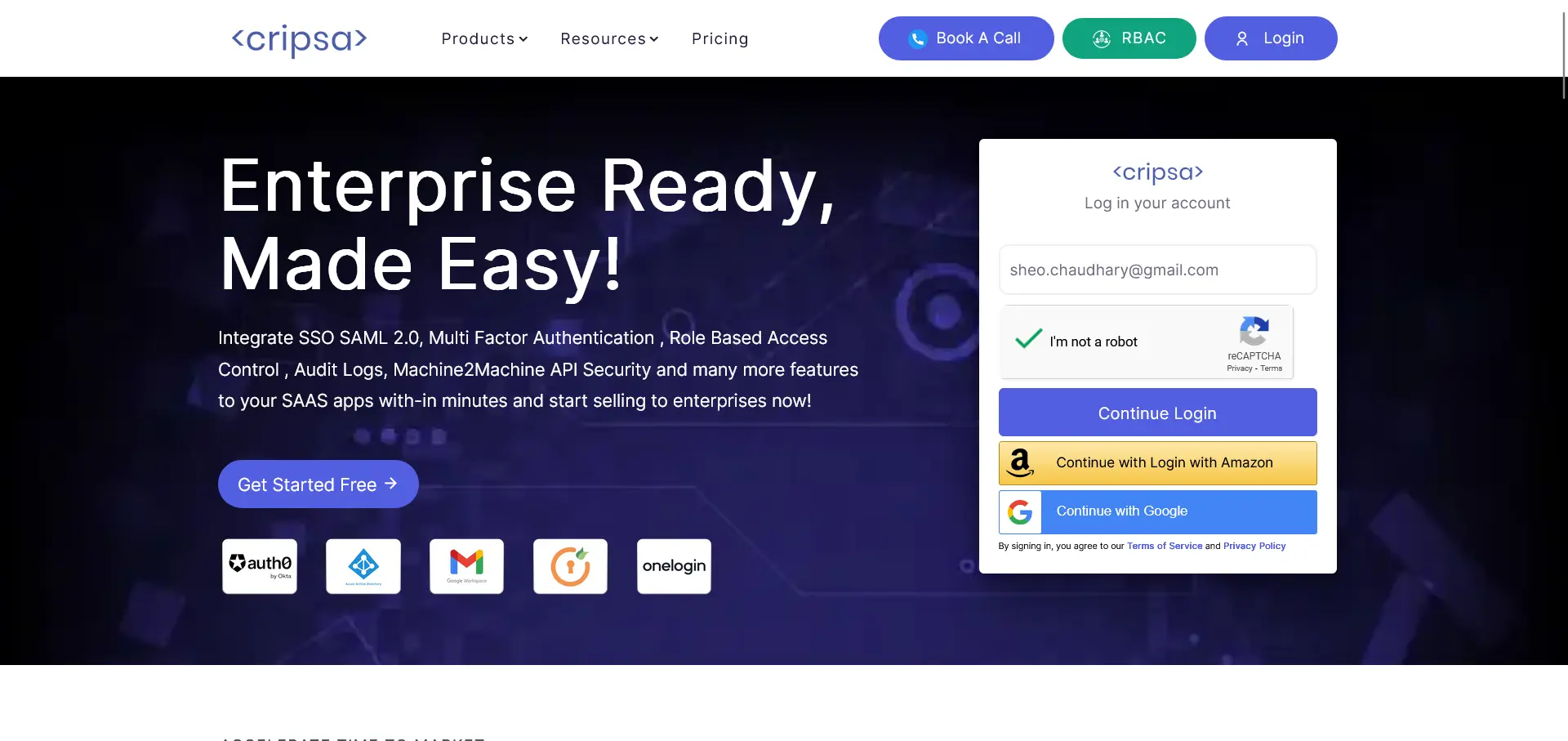
Once logged in Create project for OIDC.
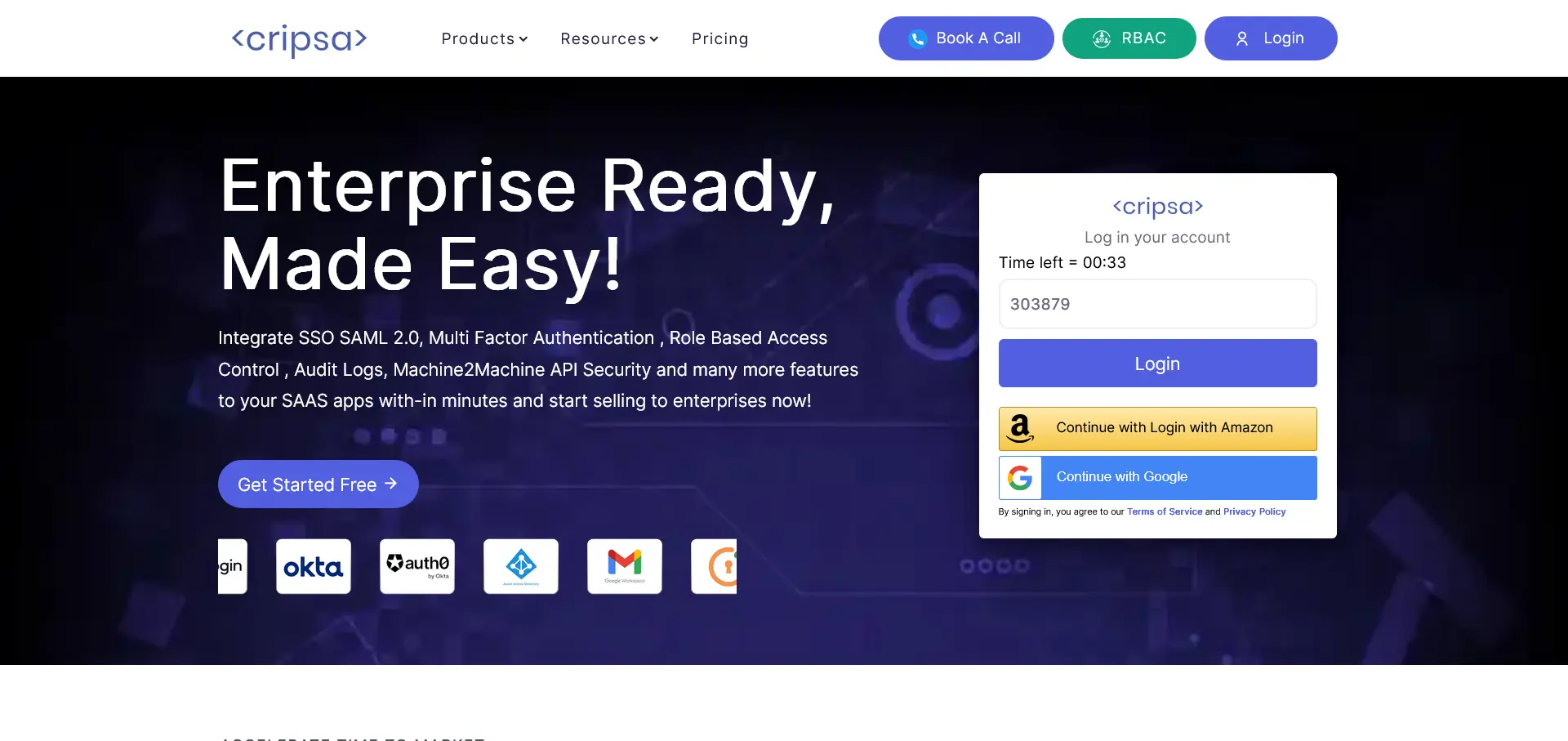
Fill all the details. All the fields are required.
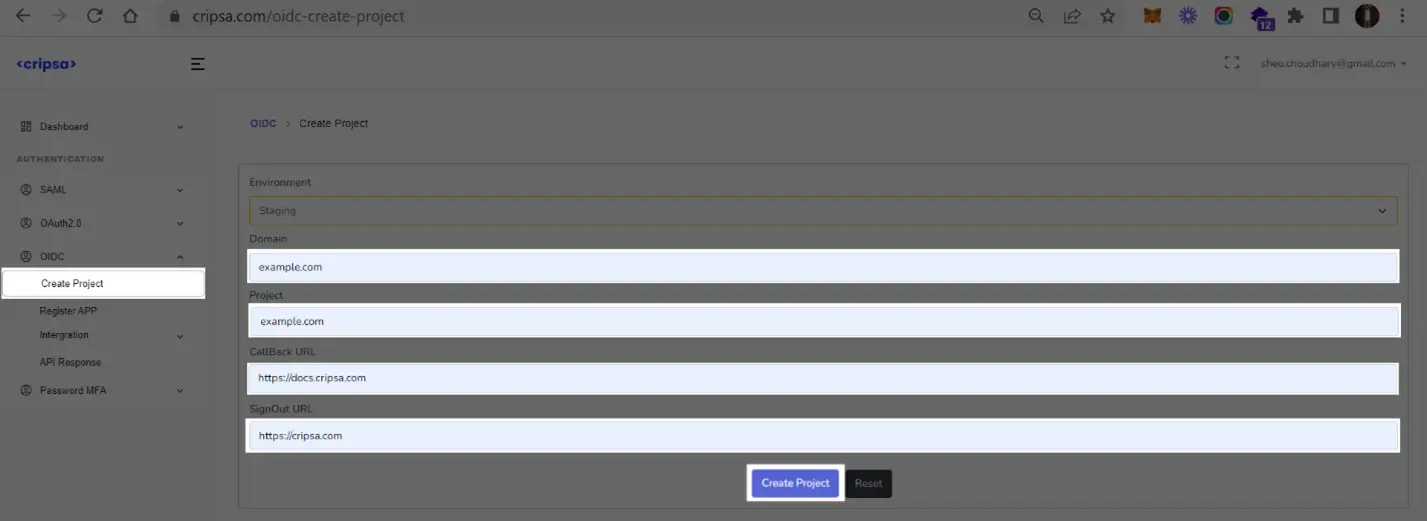
Click on “Create Project”.
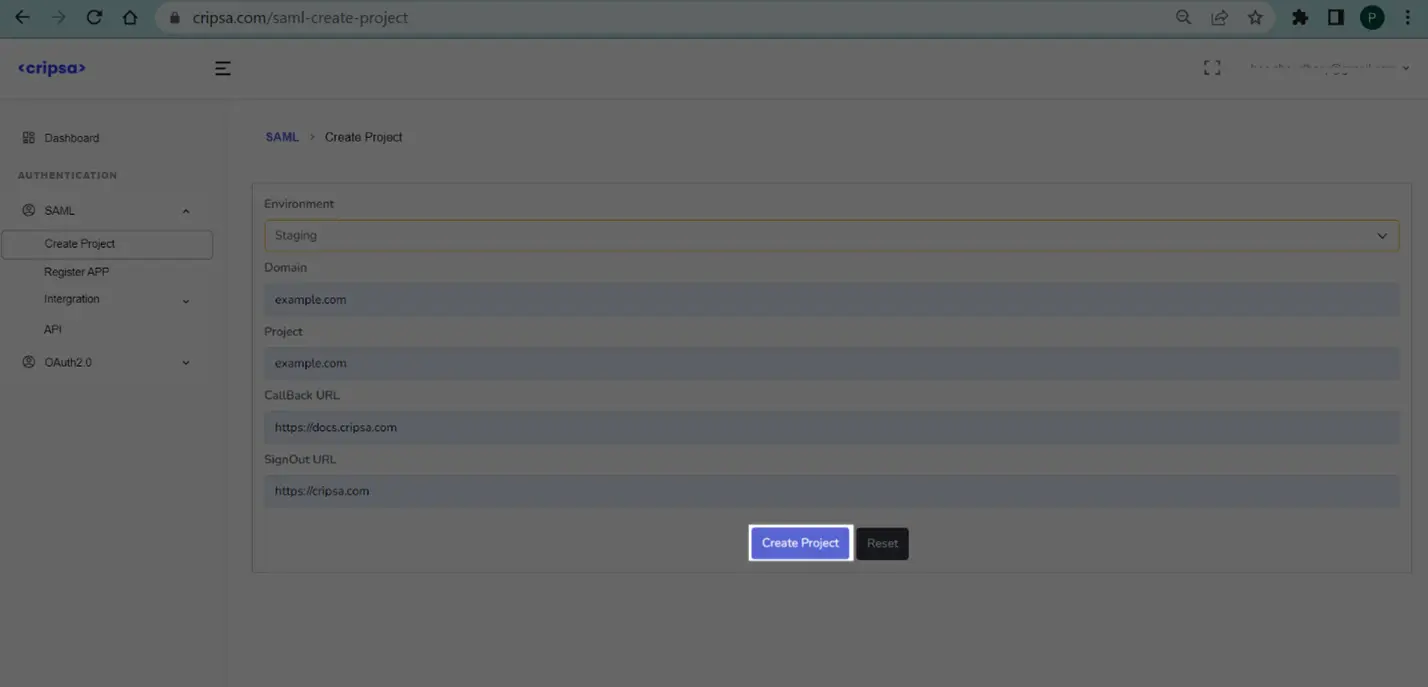
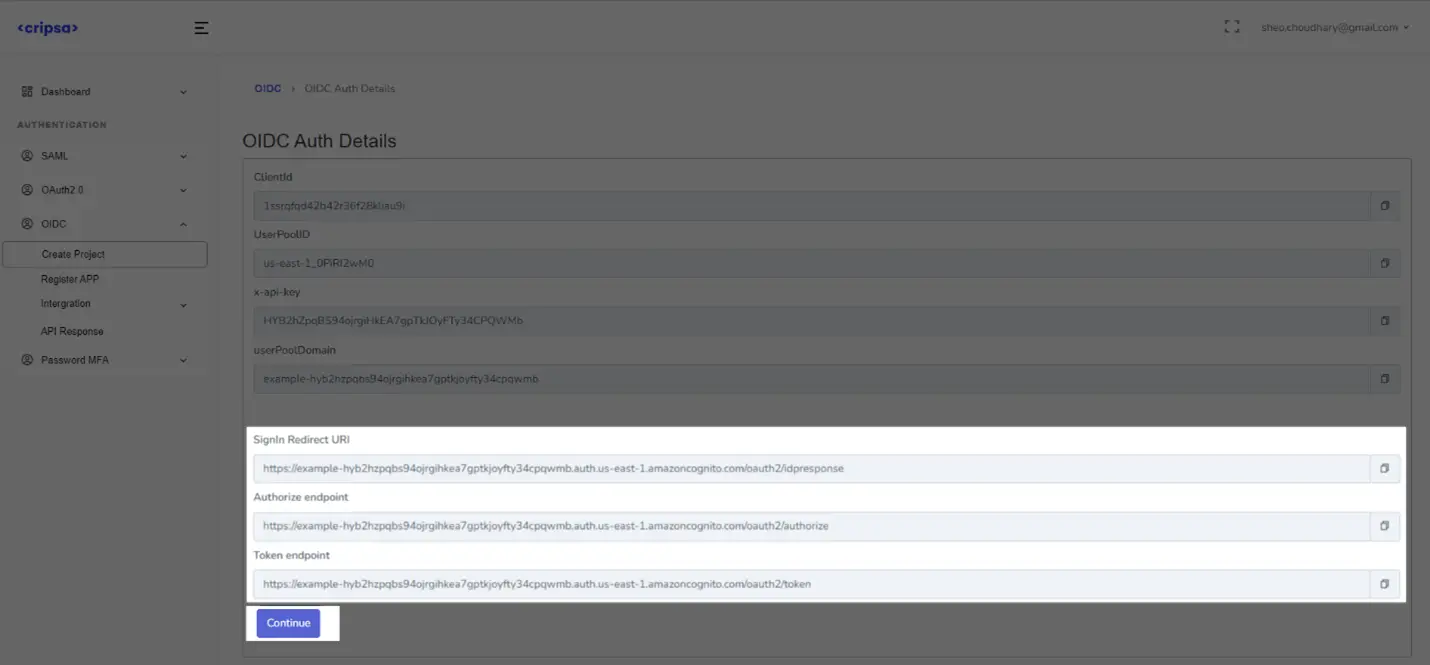
Note Down “SignIn Redirect URI” information which will be used while registering Azure OIDC App with Cripsa.
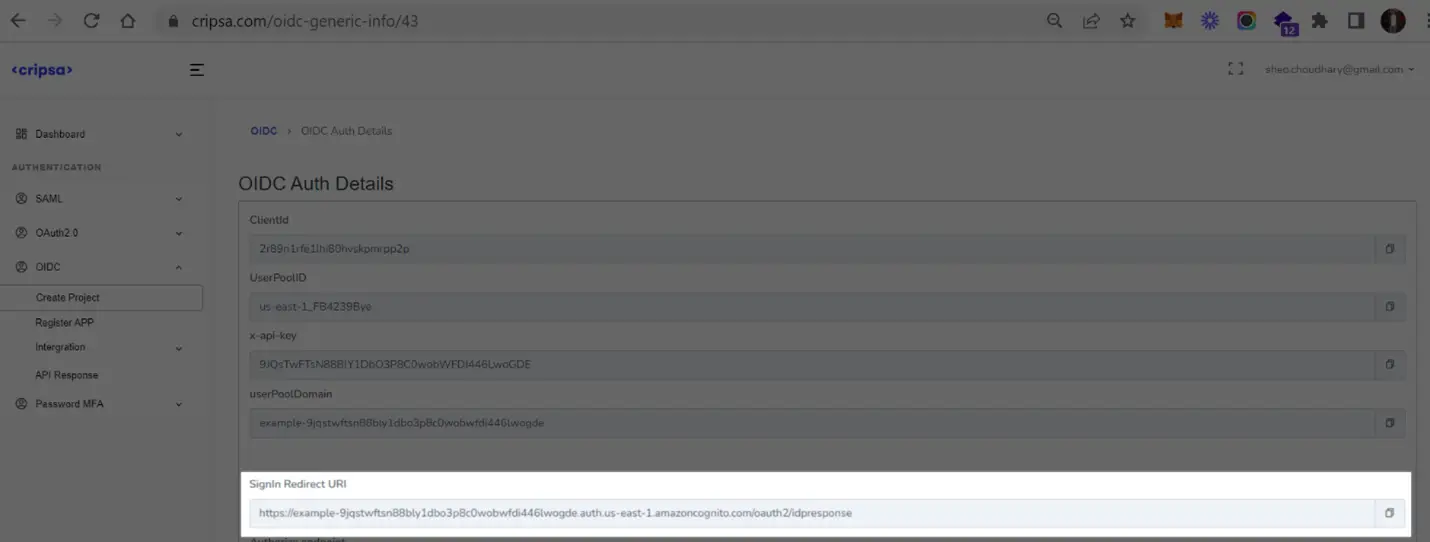
What Cripsa provides
Cripsa provides the SignIn Redirect URL. It’s readily available in your Project Detail page of Cripsa Dashboard.
The SignIn Redirect URL is the location an Identity Provider redirects its authentication response to. In Okta’s case, it needs to be set by the Enterprise when configuring your application in their Okta dashboard.
Specifically, the SignIn Redirect URL will need to be set as the “Sign-in Redirect URIs” in the “Service Provider Details” step of the Okta OIDC setup.
What you’ll need
In order to integrate you’ll need is Client Credential (ClientId and ClientSecret) and OIDC Issuer information of the Okta App.
Normally, this information will come from your Enterprise customer’s IT Management team when they set up your application’s OIDC configuration in their Azure AD admin dashboard. But should that not be the case during your setup, here’s how to obtain it.
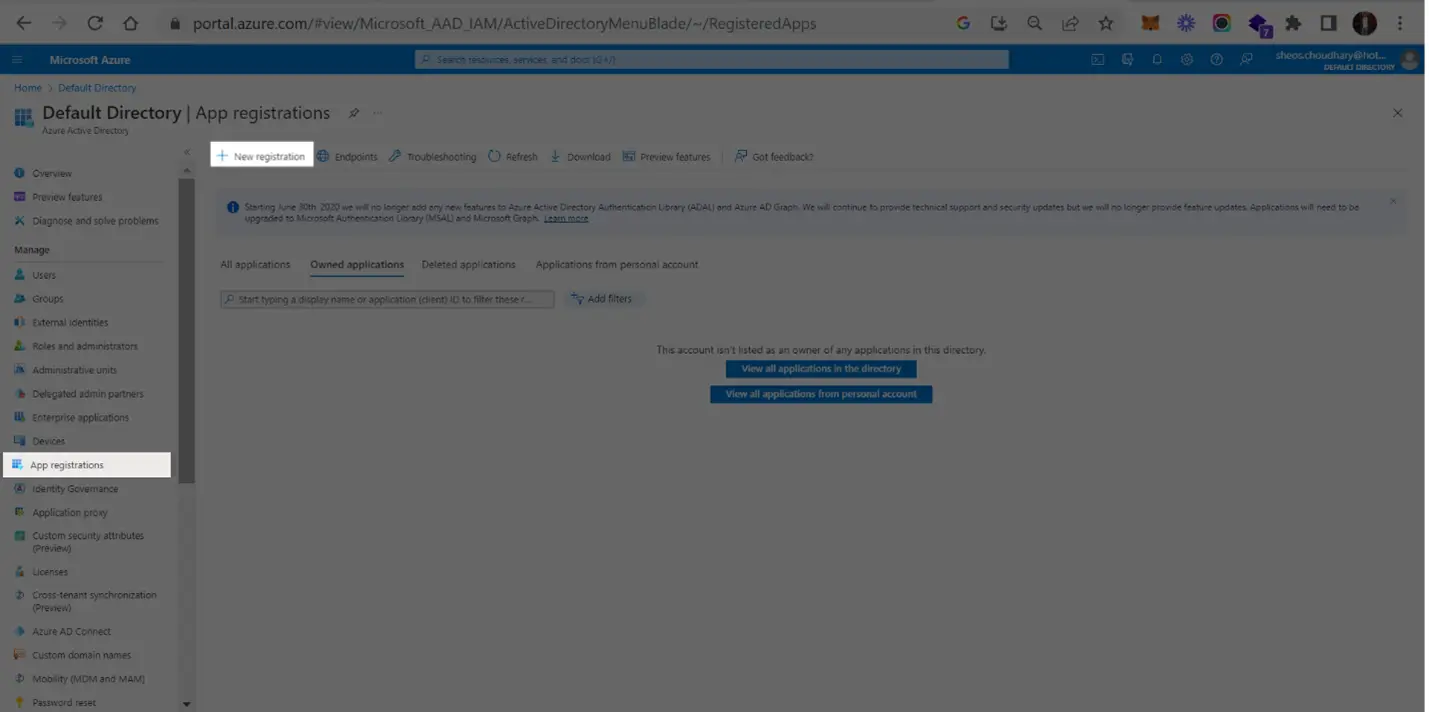
1. Log in
Open Azure Portal https://portal.azure.com/, on the right-side menu choose “Azure Active Directory-> Enterprise applications->New Application”. If your application is already created, select it from the list of applications and move to Step 6. If you haven’t created a OIDC application, select “New Application” and then provide the details.
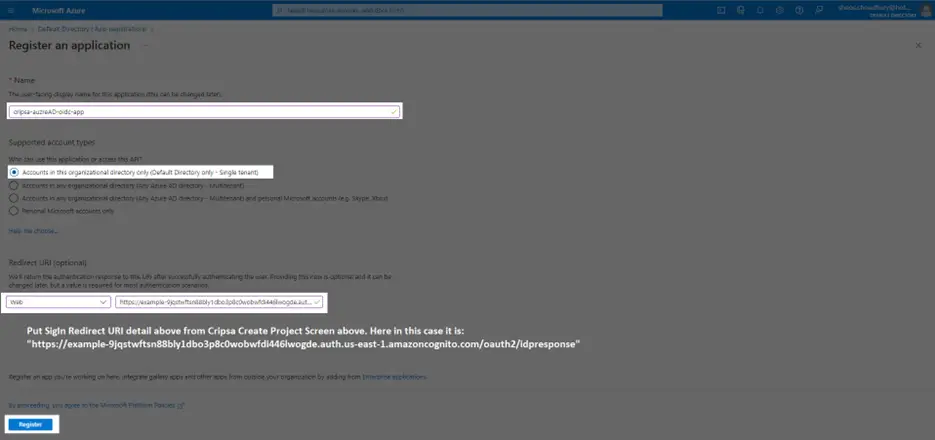
2. Enter Your App’s Information
Give the app a descriptive name and upload an icon, if applicable. Click “Continue”.
Now add a certificate
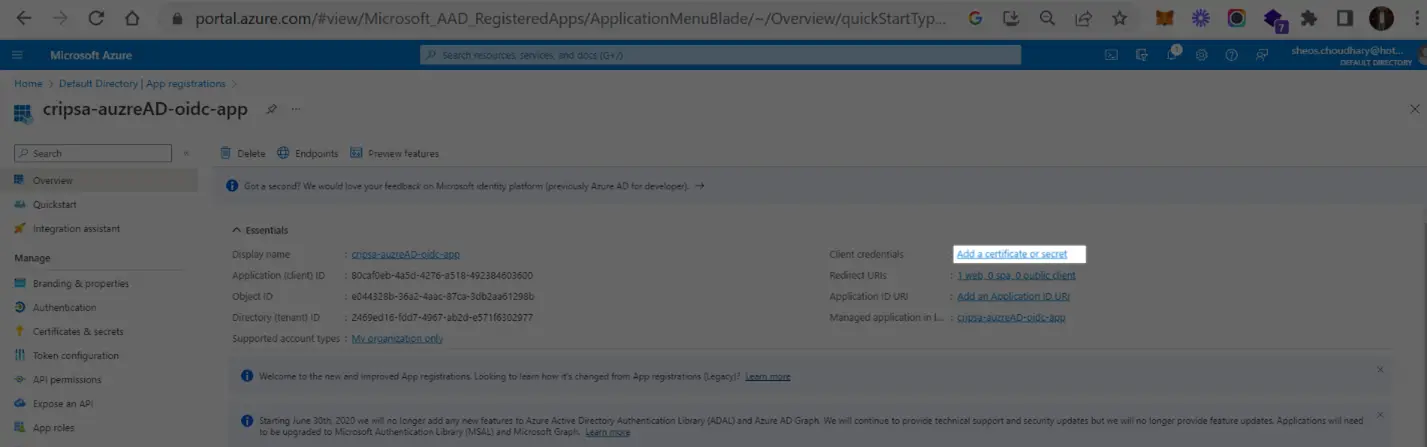
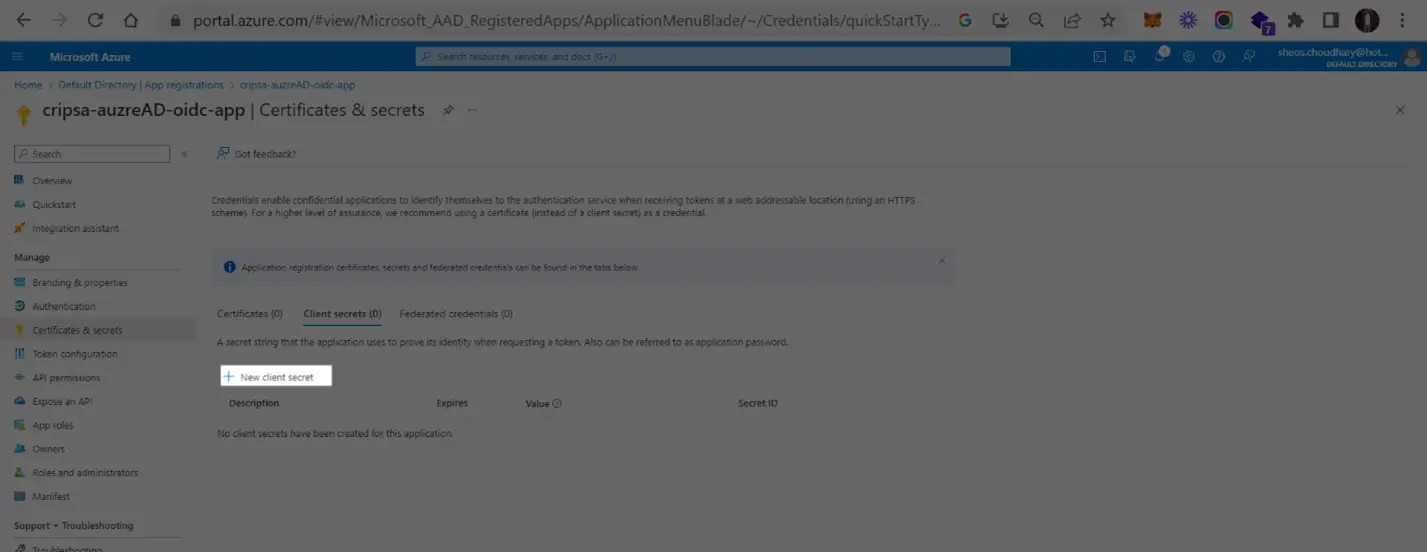
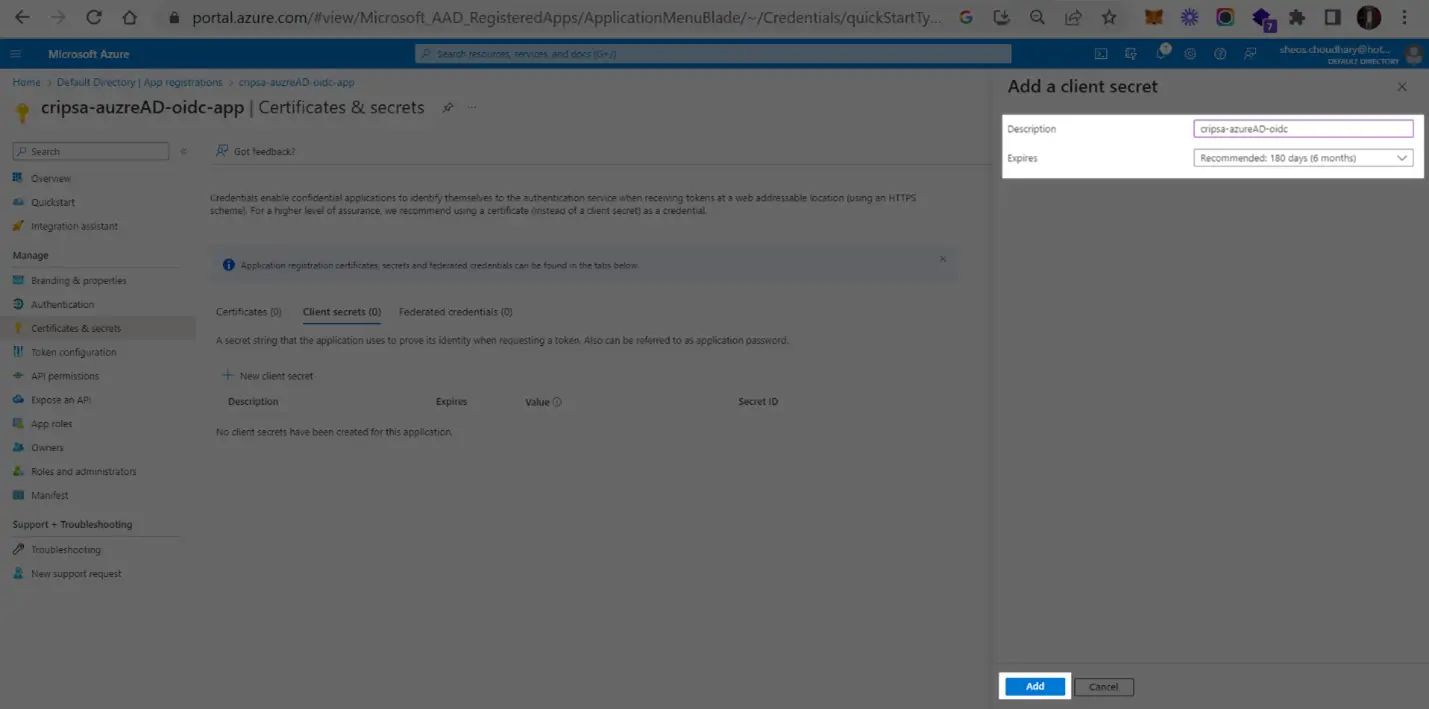
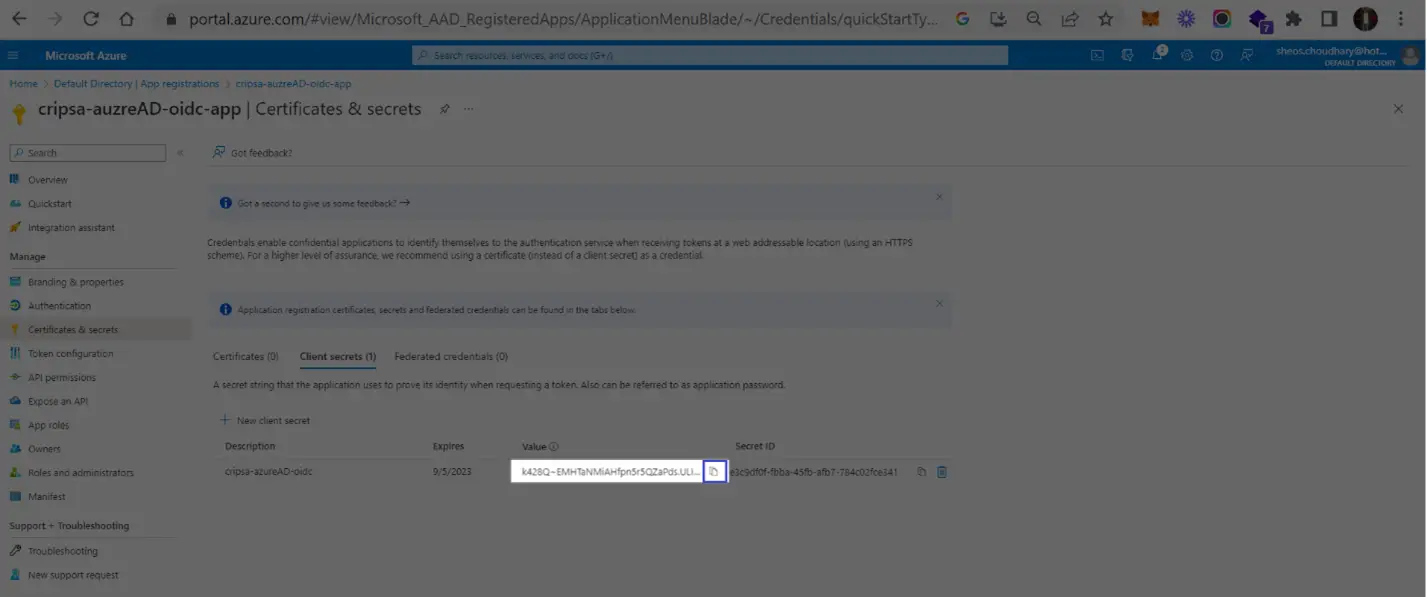
Copy the ClientSecret and ClientID
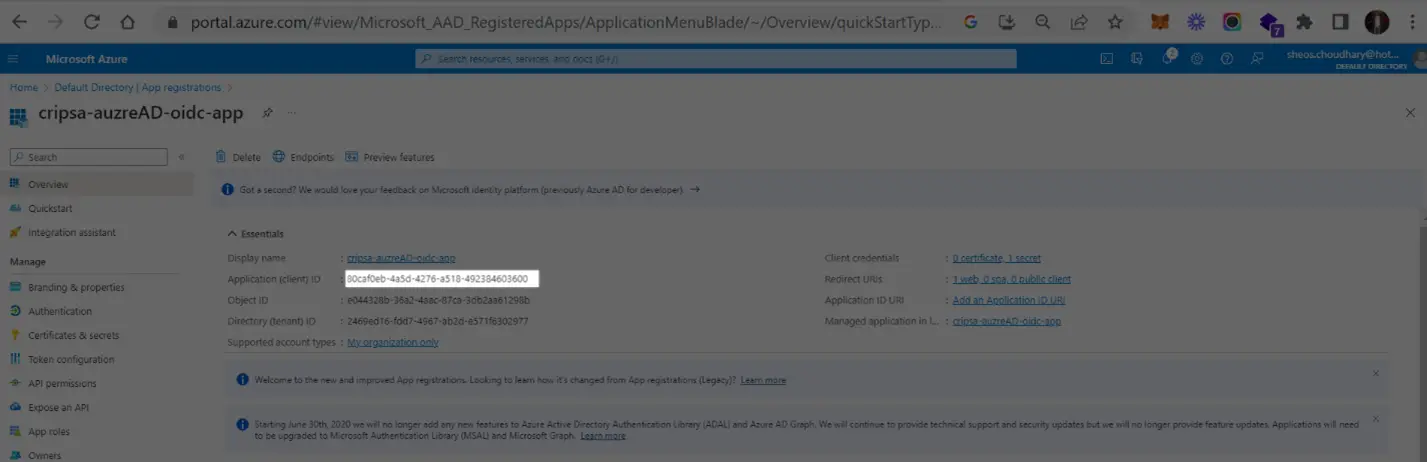
3. Obtain Client Credential
Copy the value of highlighted to get CLientId and then click on Client Credentials to get Client Secret. These two values needed for registration of OIDC app with Cripsa through Cripsa Dashboard in Step 6.
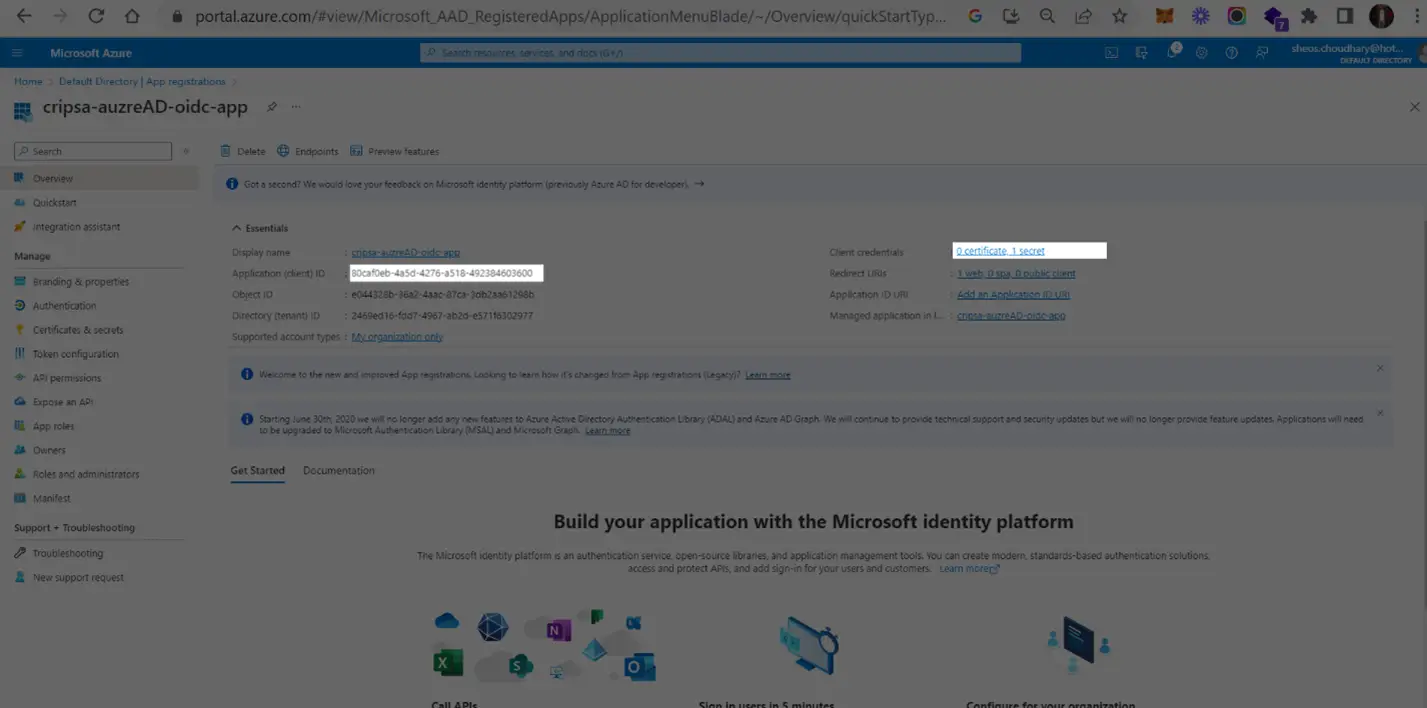
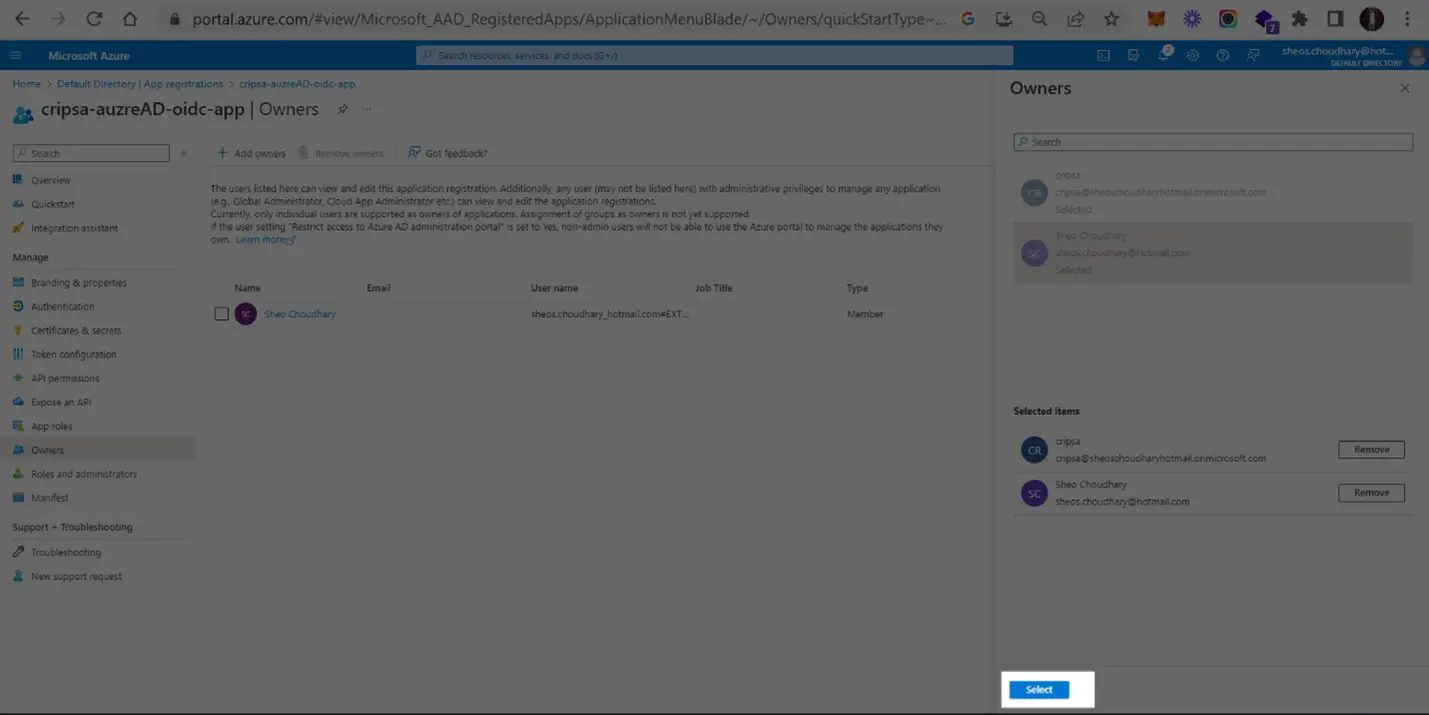
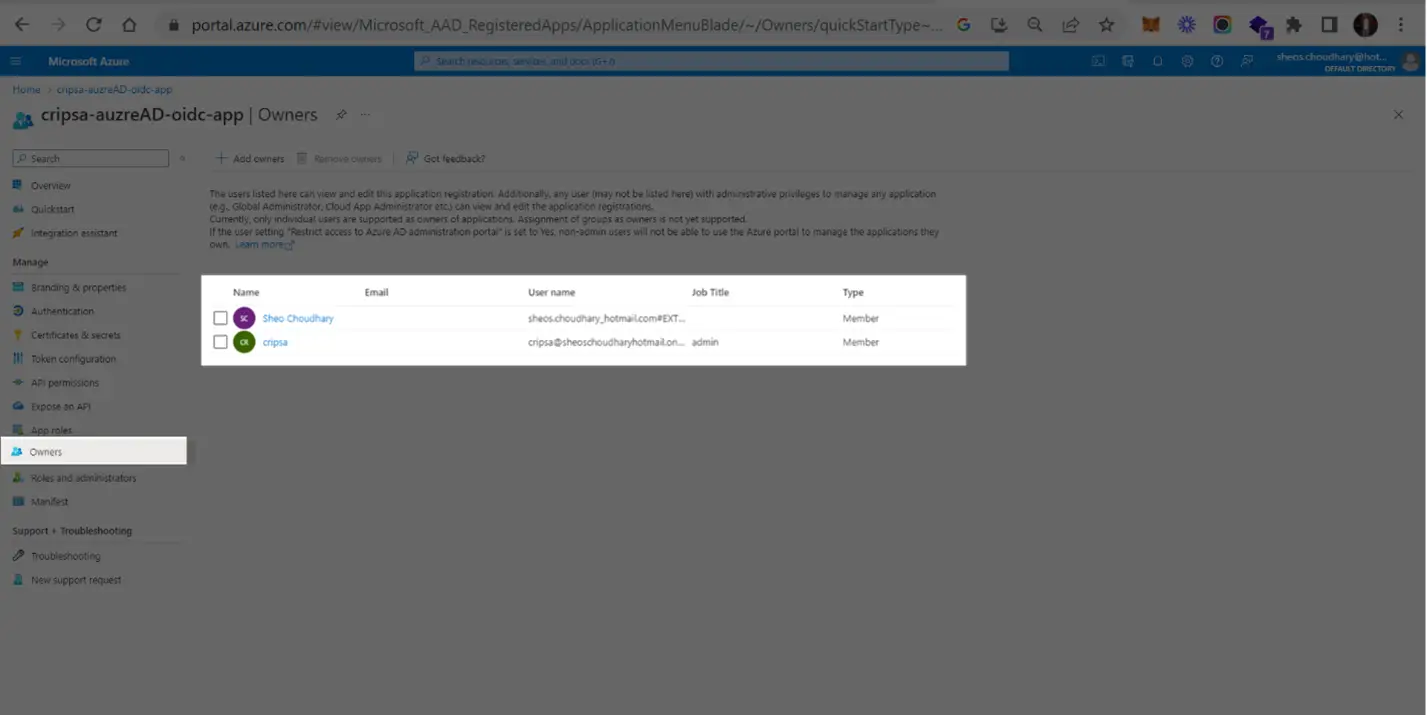
4. Adding Owners
In the Owners->Add owners, one can add users.
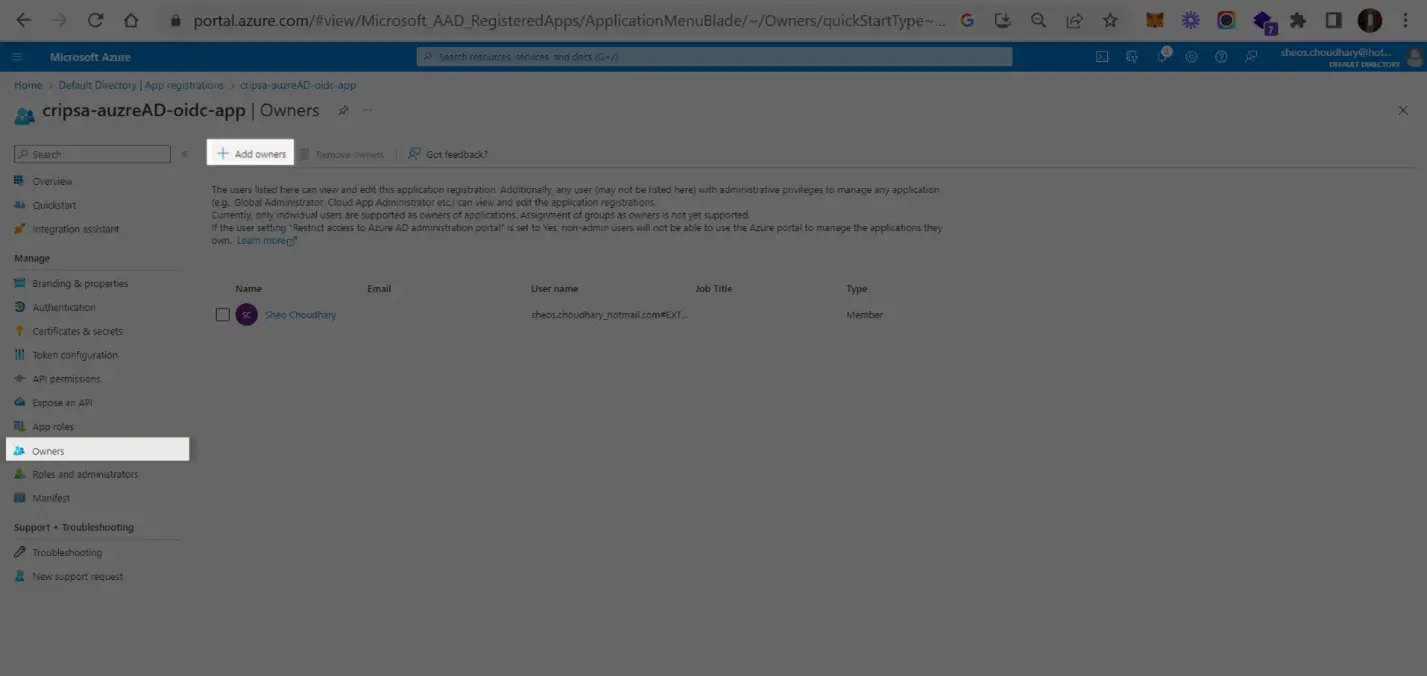
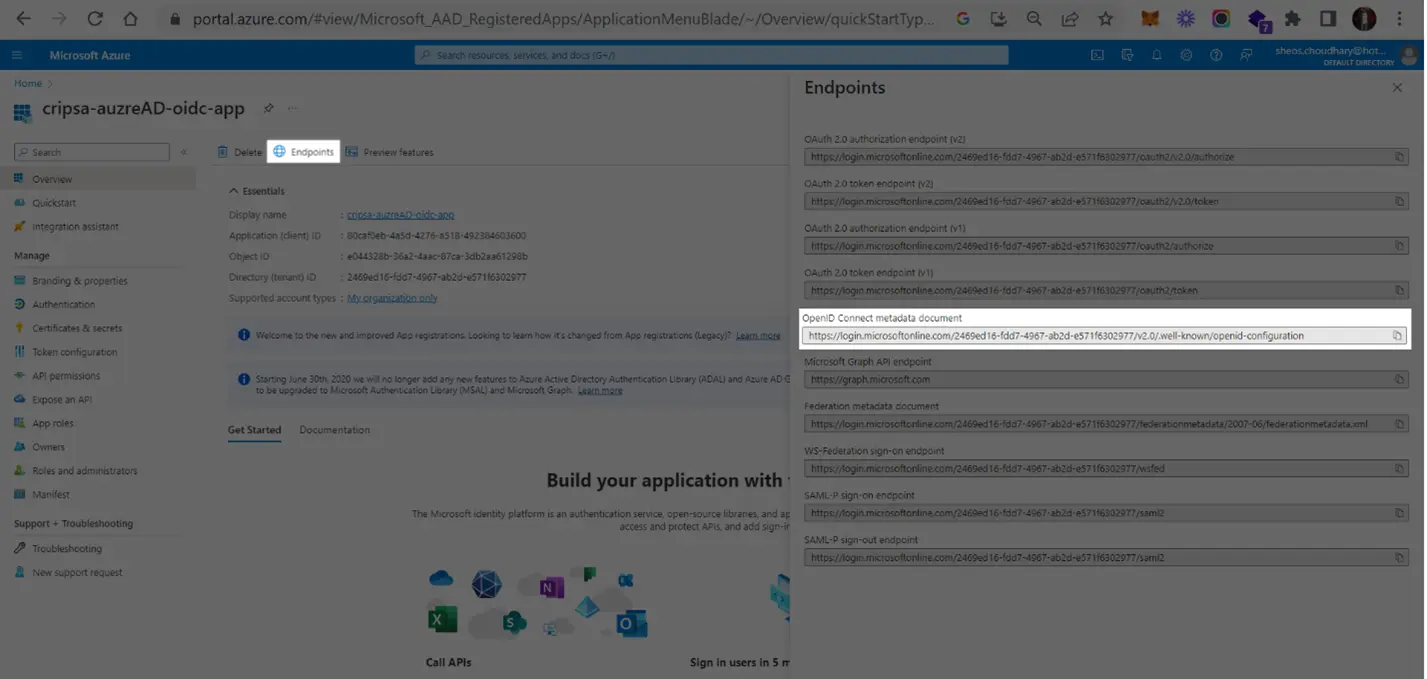
5. Getting Issuer Information
Go to Overview and click on Endpoints. Copy the OpenID Connect metadata document URI and open this in browser.
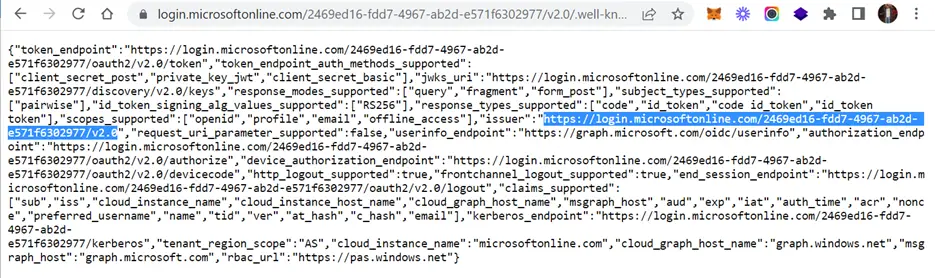
Note down the highlighted issuer information and use this also while registering the OIDC App with Cripsa.
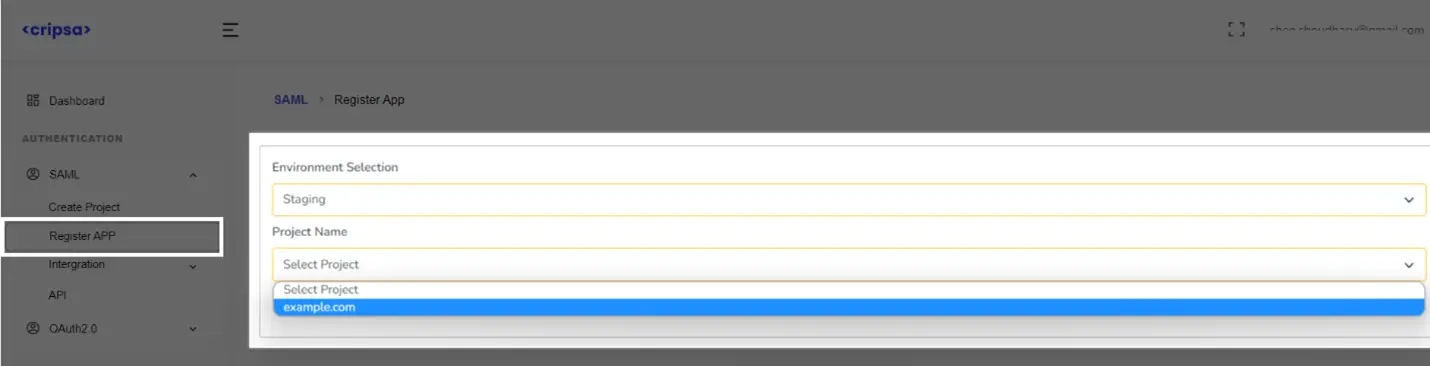
Now go back to https://cripsa.com/OIDC-register-app ->Select your project you have just created.
6. Registering OIDC App with Cripsa
Now go back to https://cripsa.com/OIDC-register-app ->Select your project you have just created.
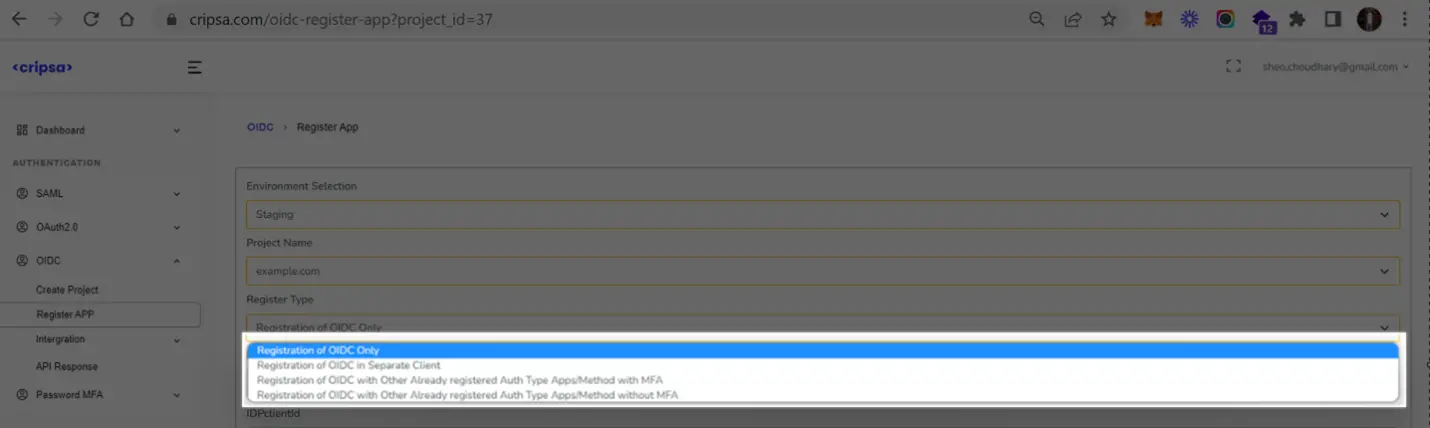
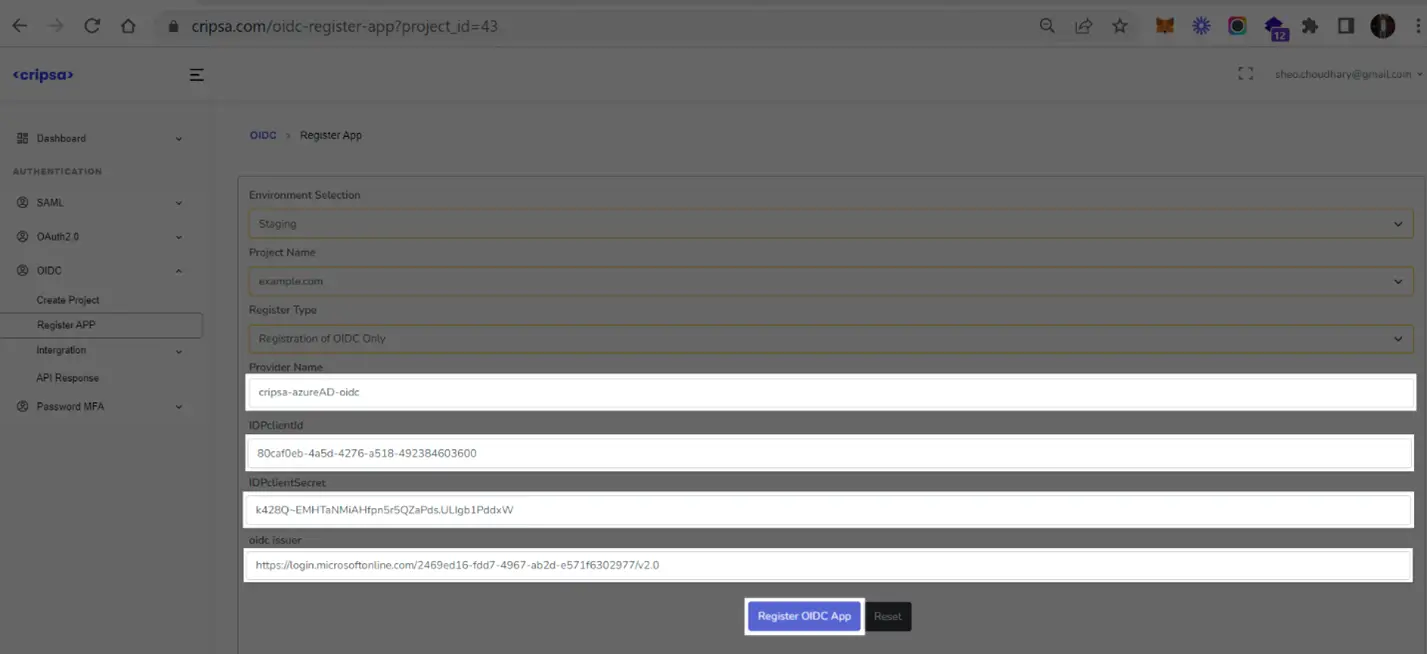
Here Three Fields are Mandatory to fill:
- Register Type
- Provider Name (name must be unique with no special character and all in small letter)
- Client Credentials (ClientId and ClientSecret)
- OIDC Issuer
In the Register Type there are four options, and one has to select anyone of them as per your requirement. For more information on these options please see FAQ.
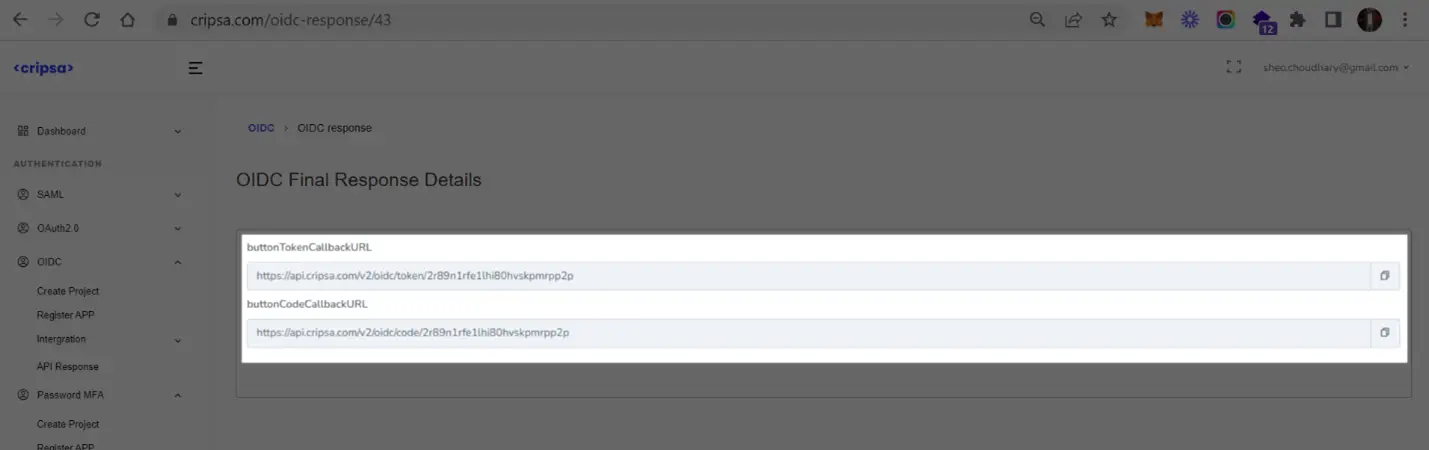
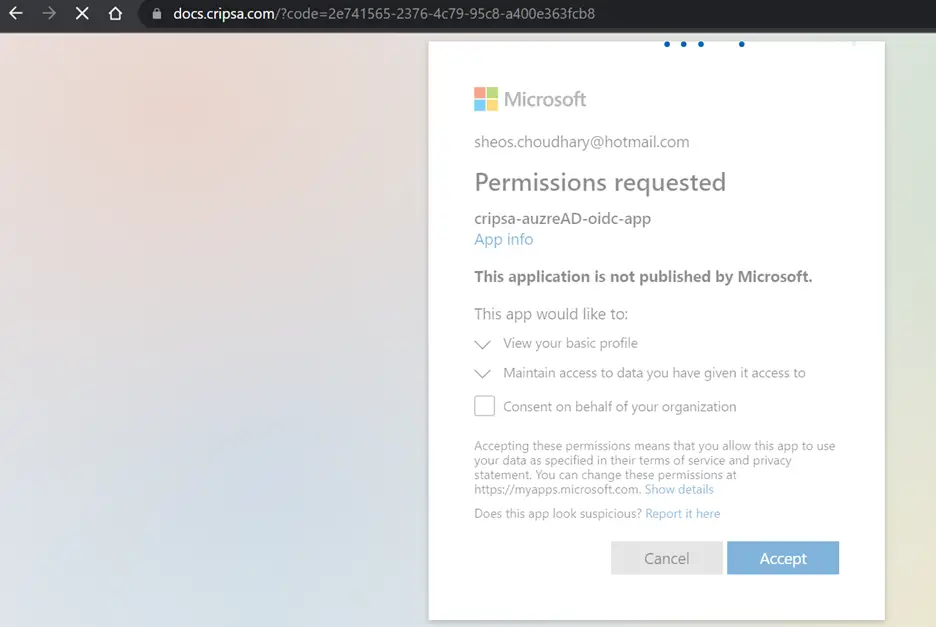
7. User Login Testing
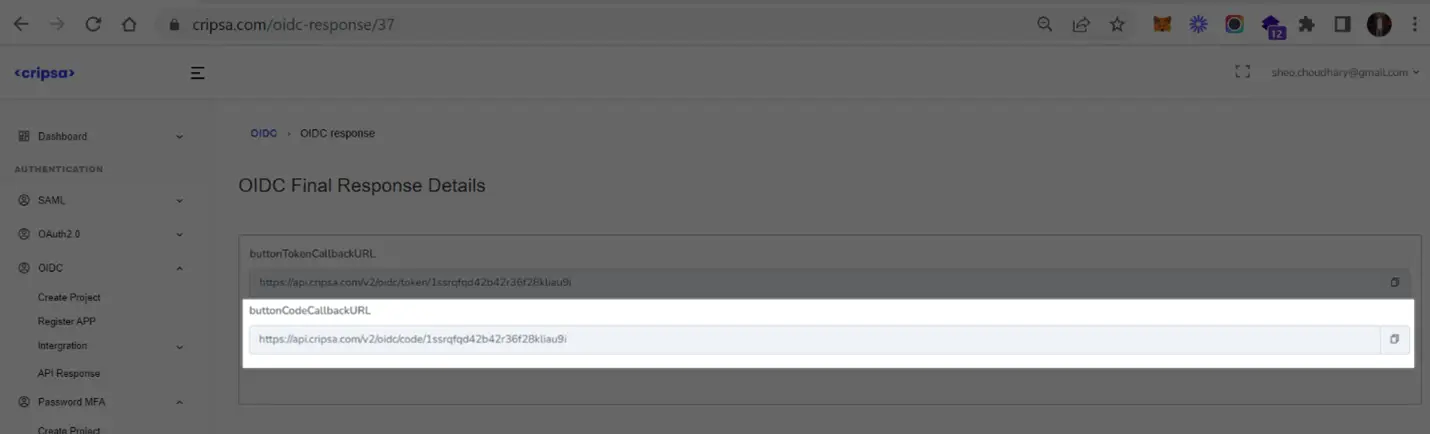
Using code URI to get code after successful login to Okta.
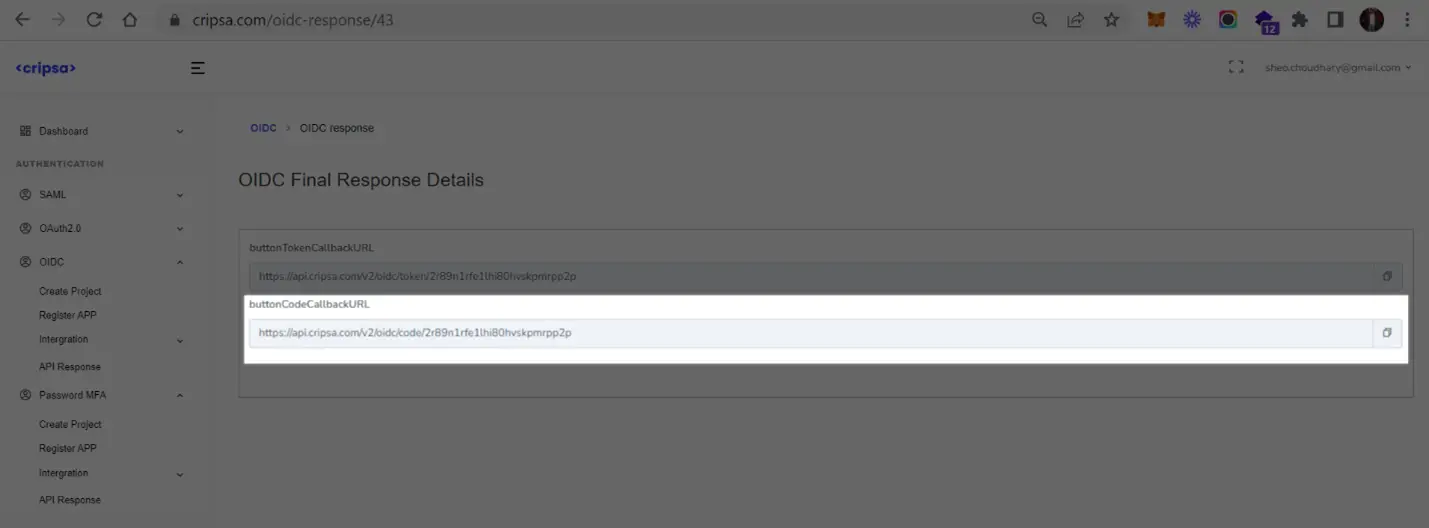
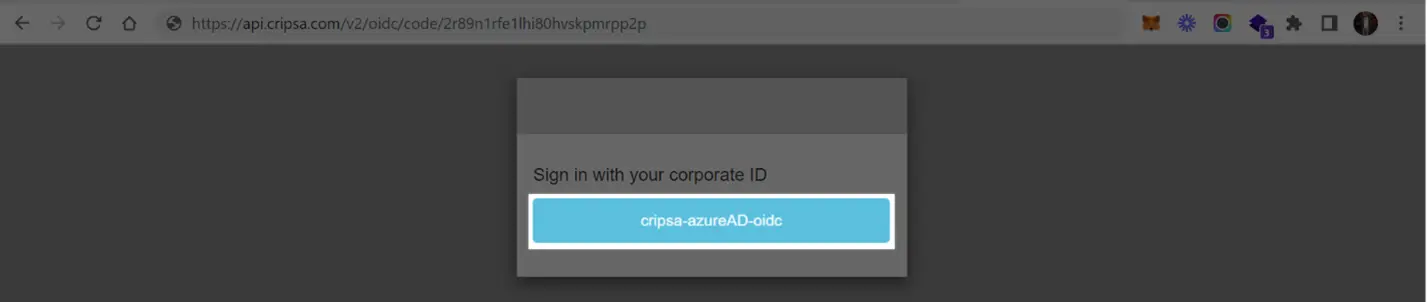
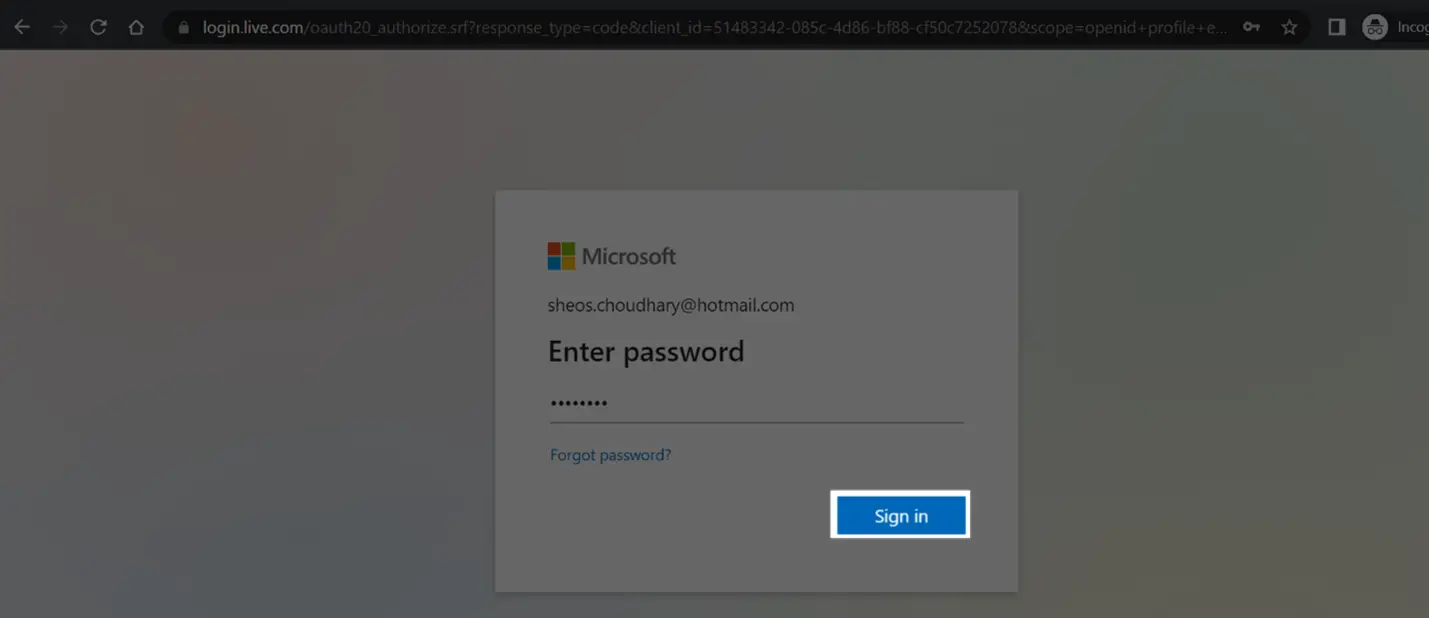
Now follow the screen instructions to login
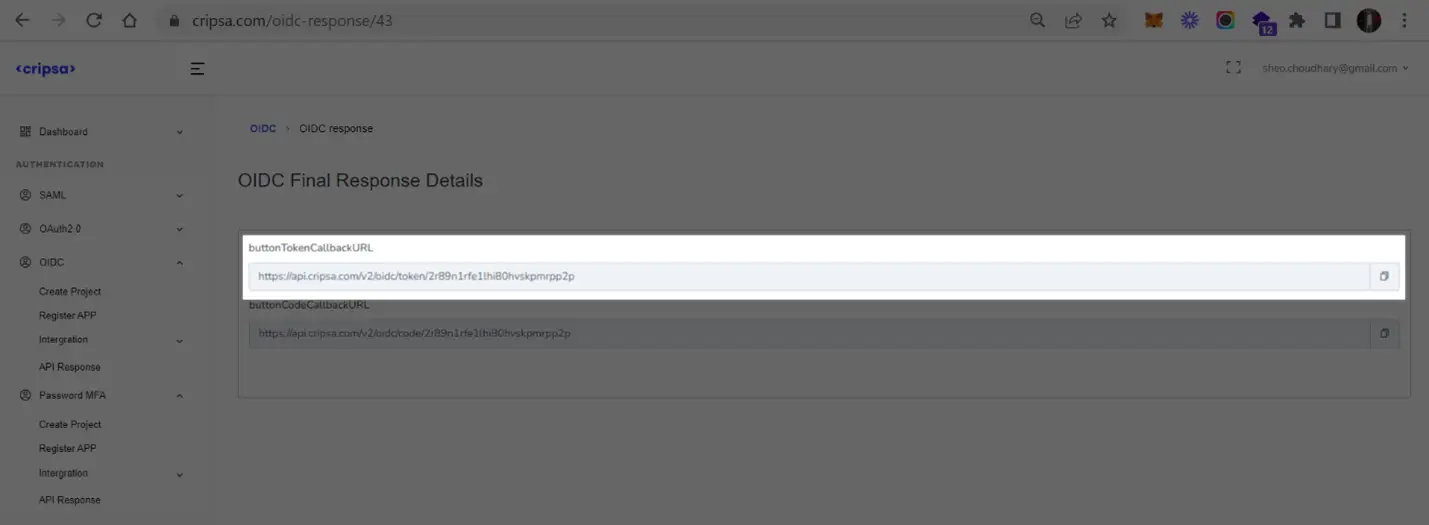
Using token URI to get accessToken after successful login to Okta.
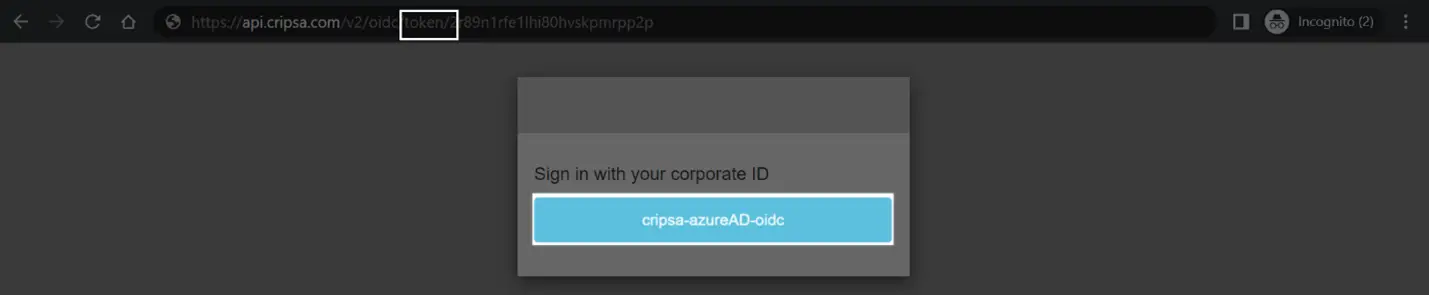
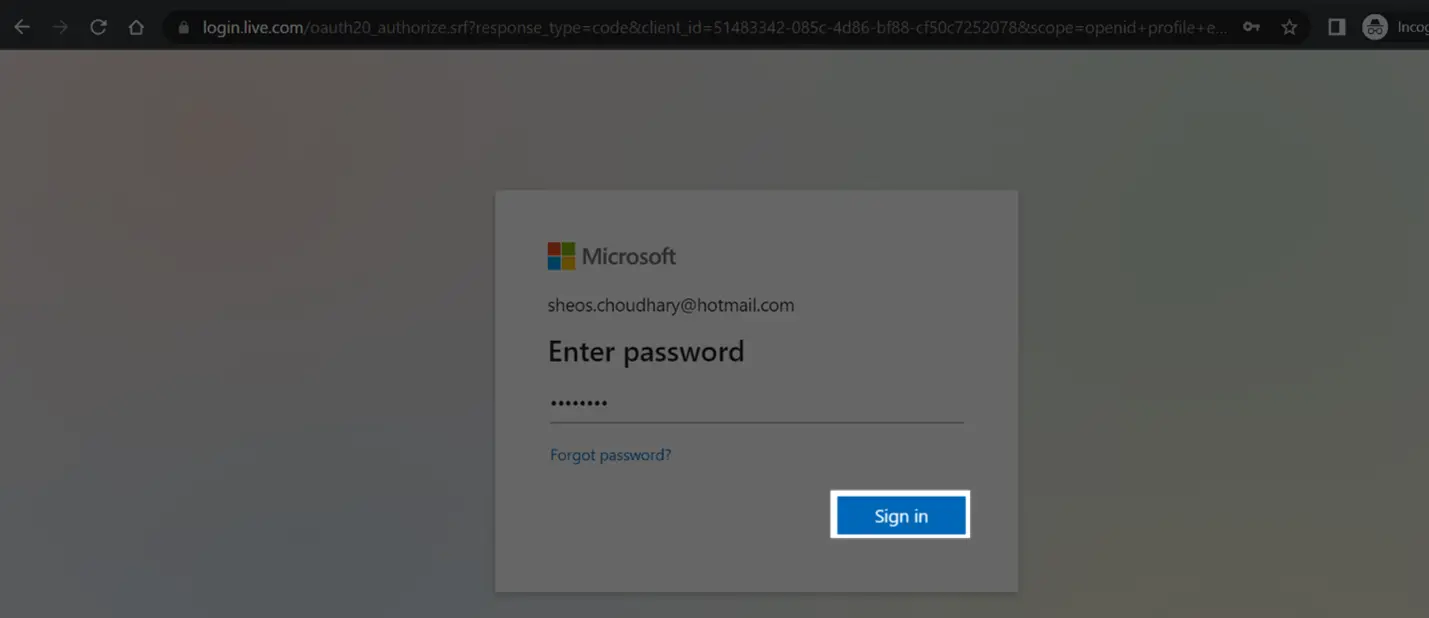
Now follow the screen instructions to login
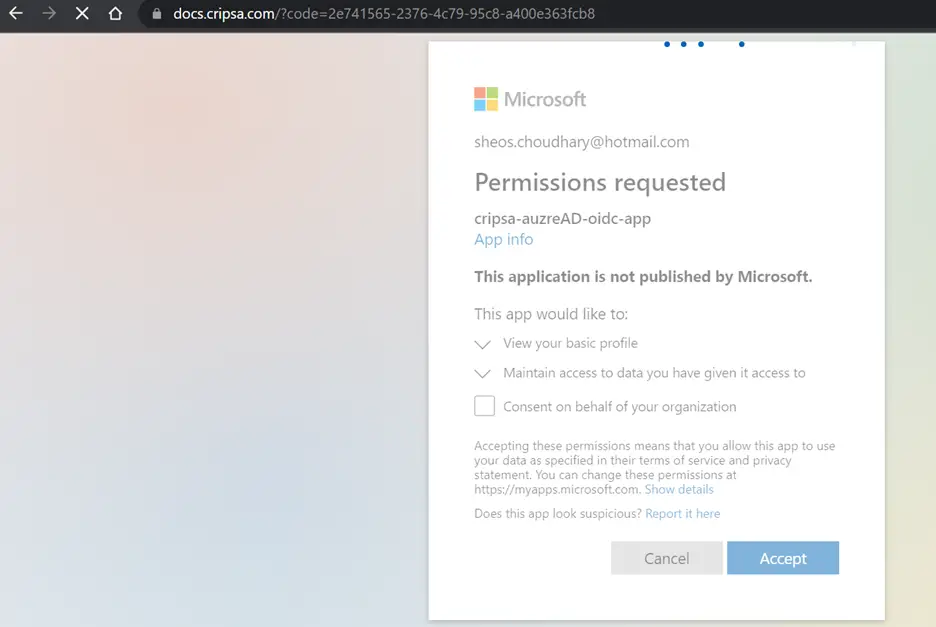
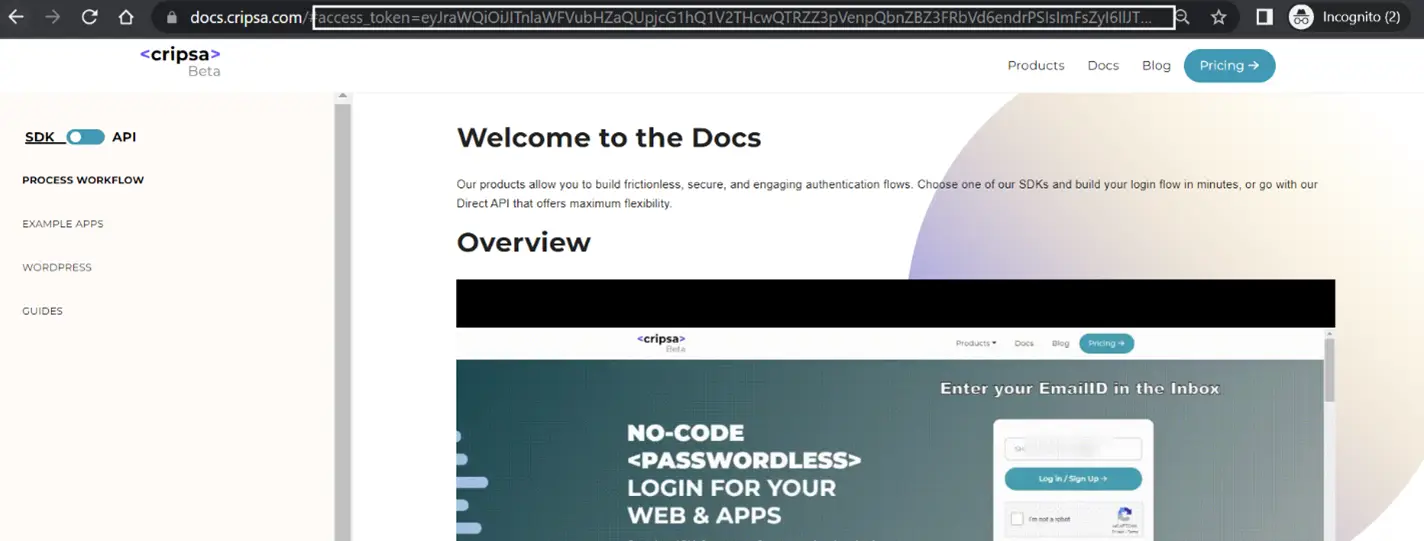
Frequently asked questions
1. How many Registration Options available in Cripsa for OIDC and what is the difference between them?
In the Register Type there are four options:
- Registration of OIDC Only
- Registration of OIDC in Separate Client
- Registration of OIDC with Other Already registered Auth Type Apps/Method+MFA
- Registration of OIDC with Other Already registered Auth Type Apps/Method without MFA
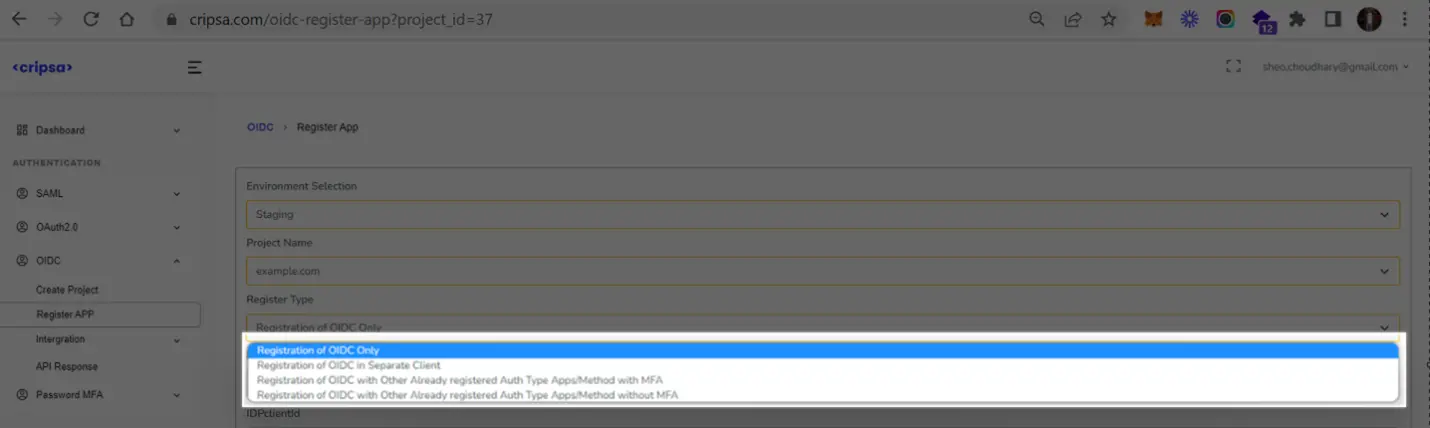
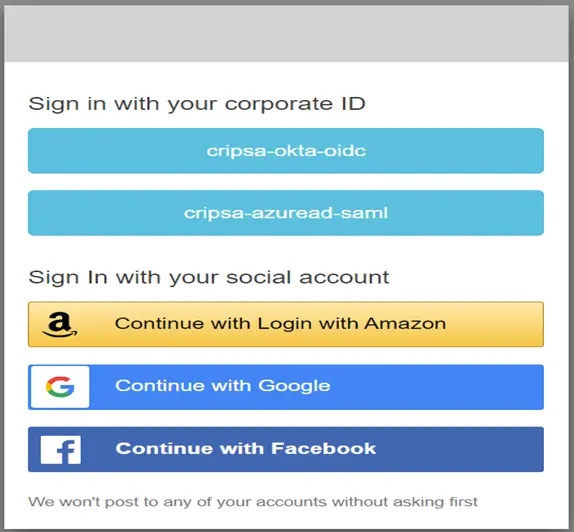
Only the Login screen would be Different for each Registration Type.
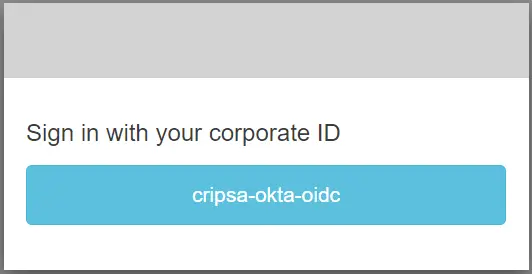
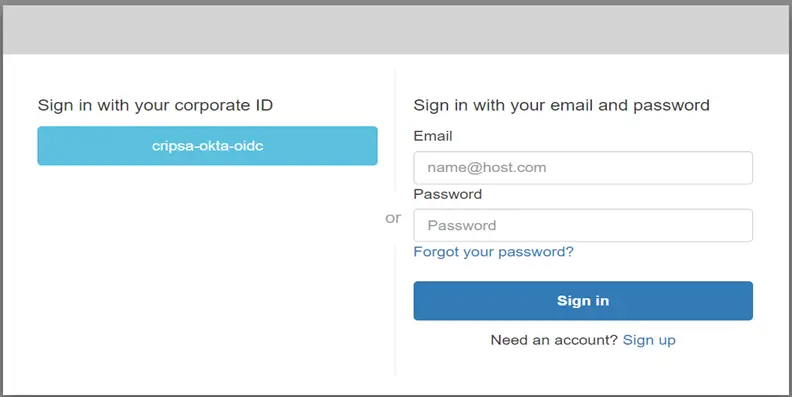
Here in the above diagram one can see MFA is available along with OIDC authentication.
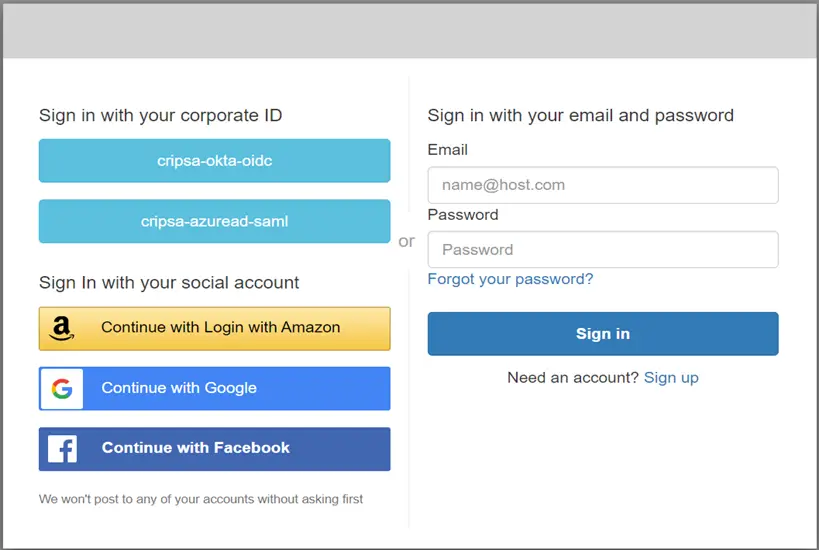
Here in the above diagram one can see MFA is available along with OIDC and AUTH 2.0 authentication.